How a Thief Looted $300,000 from Bank Accounts
In a digital era where our lives revolve around smartphones, a chilling tale from the Minnesota Correctional Facility serves as a stark reminder of our vulnerabilities. Aaron Johnson, a 26-year-old inmate, admitted to exploiting a simple passcode trick to siphon over $300,000 from unsuspecting victims’ bank accounts by hacking into their iPhones. This story isn't just a recount of a criminal's exploits; it's a wakeup call to every smartphone user and a testament to the evolving security measures in mobile technology.
The Conman's Method
Johnson's method was rudimentary yet effective. He targeted iPhone users at local bars, watching as they entered their passcodes, then swiping the phones. Once he had the device and the passcode, he changed the passwords, locking users out, and hijacked their Apple IDs. By enrolling his face in Face ID and accessing the password keychain, he had a gateway to their banking apps and personal information.
Drained Accounts and a Trail of Victims
The consequences were dire. Victims found their bank accounts emptied before they even realized their phones were missing. Johnson’s weekends could yield up to $20,000 from selling stolen phones, not counting the money drained directly from bank accounts. His predatory strategy targeted college-aged men, exploiting their trust and inebriation, leaving a trail of financial and emotional devastation.
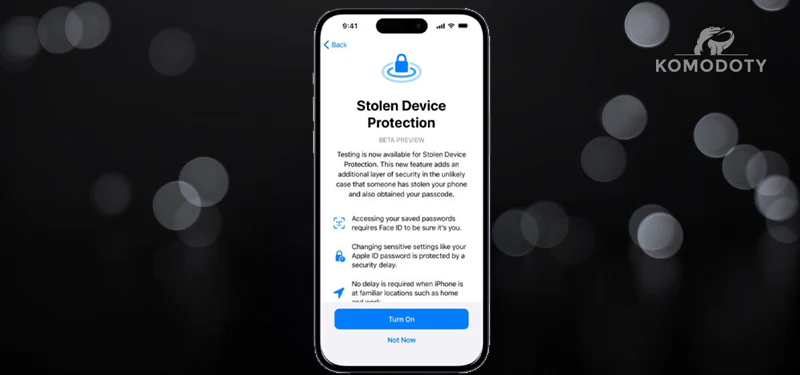
Apple's Step Toward Safer Digital Spaces
Prompted by these breaches, Apple introduced the 'Stolen Device Protection' feature in iOS 17.3. This setting is more than just an update; it's a fortress of security layers. It utilizes biometrics and geolocation, making it significantly harder for thieves to impersonate the owner. If an unauthorized user attempts to make critical changes from an unfamiliar location, the device locks down, requiring multiple biometric verifications.
A Cautionary Tale: The Need for Vigilance
However, no system is impervious. Vulnerabilities persist, especially if apps and services aren't secured with additional passwords or PINs. The Wall Street Journal advises extra layers of security on financial apps and swift action to remotely wipe stolen devices. Remember, technology is a tool, and its safety depends largely on how we wield it.



Leave a comment
This site is protected by hCaptcha and the hCaptcha Privacy Policy and Terms of Service apply.